VR-S1000ログ出力例9~11
Q
VR-S1000ログ出力例9~11
A
ログ出力例 9~11
VR-S1000のファームウェアVerによって出力されるログ情報が異なります。
下記はファームウェアVer.2.09以降でのログ出力例です。
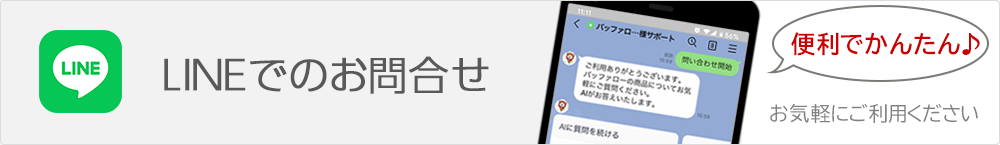
9.【失敗例】IKE Policy 認証方式が間違っていてつながらない
DUT1側のログ
PC1→PC2宛のpingでIPsecのトリガとする。 (DUT1がイニシエーターとなる)
《IPsecパラメーター》
DUT1 IKEポリシー / SHA-256
DUT2 IKEポリシー / SHA-1 : デフォルト
他は IPsecウィザードのデフォルト値で設定
Mar 24 10:47:33 VRB0C745BF000E pluto: loading secrets from "/etc/ipsec.secrets"
Mar 24 10:47:34 VRB0C745BF000E janus_run: Starting janus watcher...
Mar 24 10:47:34 VRB0C745BF000E janus watcher[12826]: Starting Janus - Dynamic DNS watcher (Version 1.3)
Mar 24 10:47:49 VRB0C745BF000E pluto: initiate on demand from 192.168.100.100:8 to 192.168.101.100:0 proto=1 state: fos_start because: acquire
Mar 24 10:47:49 VRB0C745BF000E pluto: "IPsec_test" #6: initiating Main Mode
Mar 24 10:47:49 VRB0C745BF000E pluto: "IPsec_test" #6: ignoring informational payload, type NO_PROPOSAL_CHOSEN msgid=00000000
Mar 24 10:47:49 VRB0C745BF000E pluto: "IPsec_test" #6: received and ignored informational message
Mar 24 10:47:59 VRB0C745BF000E pluto: "IPsec_test" #6: ignoring informational payload, type NO_PROPOSAL_CHOSEN msgid=00000000
Mar 24 10:47:59 VRB0C745BF000E pluto: "IPsec_test" #6: received and ignored informational message
Mar 24 10:48:19 VRB0C745BF000E pluto: "IPsec_test" #6: received and ignored informational message
Mar 24 10:48:59 VRB0C745BF000E pluto: "IPsec_test" #6: max number of retransmissions (2) reached STATE_MAIN_I1. No response (or no acceptable response) to our first IKE message
Mar 24 10:48:59 VRB0C745BF000E pluto: "IPsec_test" #6: starting keying attempt 2 of at most 3
Mar 24 10:48:59 VRB0C745BF000E pluto: "IPsec_test" #7: initiating Main Mode to replace #6
Mar 24 10:48:59 VRB0C745BF000E pluto: "IPsec_test" #7: ignoring informational payload, type NO_PROPOSAL_CHOSEN msgid=00000000
Mar 24 10:48:59 VRB0C745BF000E pluto: "IPsec_test" #7: received and ignored informational message
Mar 24 10:49:09 VRB0C745BF000E pluto: "IPsec_test" #7: received and ignored informational message
Mar 24 10:49:29 VRB0C745BF000E pluto: "IPsec_test" #7: ignoring informational payload, type NO_PROPOSAL_CHOSEN msgid=00000000
Mar 24 10:49:29 VRB0C745BF000E pluto: "IPsec_test" #7: received and ignored informational message
Mar 24 10:50:09 VRB0C745BF000E pluto: "IPsec_test" #7: starting keying attempt 3 of at most 3
Mar 24 10:50:09 VRB0C745BF000E pluto: "IPsec_test" #8: initiating Main Mode to replace #7
Mar 24 10:50:09 VRB0C745BF000E pluto: "IPsec_test" #8: ignoring informational payload, type NO_PROPOSAL_CHOSEN msgid=00000000
Mar 24 10:50:09 VRB0C745BF000E pluto: "IPsec_test" #8: received and ignored informational message
Mar 24 10:50:19 VRB0C745BF000E pluto: "IPsec_test" #8: ignoring informational payload, type NO_PROPOSAL_CHOSEN msgid=00000000
Mar 24 10:50:19 VRB0C745BF000E pluto: "IPsec_test" #8: received and ignored informational message
Mar 24 10:50:39 VRB0C745BF000E pluto: "IPsec_test" #8: ignoring informational payload, type NO_PROPOSAL_CHOSEN msgid=00000000
Mar 24 10:50:39 VRB0C745BF000E pluto: "IPsec_test" #8: received and ignored informational message
DUT2側のログ
MEMO
Mainモードで接続要求に応答しているが、双方の提案が不一致のため、Phase1(ISAKMP SA)に失敗している。
Mar 24 10:47:49 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:47:49 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:47:49 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:47:49 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:47:49 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:47:49 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:47:49 VRB0C745BF0018 pluto: "IPsec_DUT2" #12: responding to Main Mode
Mar 24 10:47:49 VRB0C745BF0018 pluto: "IPsec_DUT2" #12: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA2_256, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 10:47:49 VRB0C745BF0018 pluto: "IPsec_DUT2" #12: no acceptable Oakley Transform
Mar 24 10:47:49 VRB0C745BF0018 pluto: "IPsec_DUT2" #12: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.100:500
Mar 24 10:47:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Openswan (this version) VR-S1000_V2.09_D20140225-dirty ]
Mar 24 10:47:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:47:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:47:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:47:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:47:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:47:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:47:59 VRB0C745BF0018 pluto: "IPsec_DUT2" #13: responding to Main Mode
Mar 24 10:47:59 VRB0C745BF0018 pluto: "IPsec_DUT2" #13: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA2_256, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 10:47:59 VRB0C745BF0018 pluto: "IPsec_DUT2" #13: no acceptable Oakley Transform
Mar 24 10:47:59 VRB0C745BF0018 pluto: "IPsec_DUT2" #13: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.100:500
Mar 24 10:48:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:48:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:48:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:48:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:48:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:48:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:48:19 VRB0C745BF0018 pluto: "IPsec_DUT2" #14: responding to Main Mode
Mar 24 10:48:19 VRB0C745BF0018 pluto: "IPsec_DUT2" #14: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA2_256, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 10:48:19 VRB0C745BF0018 pluto: "IPsec_DUT2" #14: no acceptable Oakley Transform
Mar 24 10:48:19 VRB0C745BF0018 pluto: "IPsec_DUT2" #14: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.100:500
Mar 24 10:48:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Openswan (this version) VR-S1000_V2.09_D20140225-dirty ]
Mar 24 10:48:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:48:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:48:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:48:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:48:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:48:59 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:48:59 VRB0C745BF0018 pluto: "IPsec_DUT2" #15: responding to Main Mode
Mar 24 10:48:59 VRB0C745BF0018 pluto: "IPsec_DUT2" #15: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA2_256, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 10:48:59 VRB0C745BF0018 pluto: "IPsec_DUT2" #15: no acceptable Oakley Transform
Mar 24 10:48:59 VRB0C745BF0018 pluto: "IPsec_DUT2" #15: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.100:500
Mar 24 10:49:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:49:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:49:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:49:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:49:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:49:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:49:09 VRB0C745BF0018 pluto: "IPsec_DUT2" #16: responding to Main Mode
Mar 24 10:49:09 VRB0C745BF0018 pluto: "IPsec_DUT2" #16: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA2_256, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 10:49:09 VRB0C745BF0018 pluto: "IPsec_DUT2" #16: no acceptable Oakley Transform
Mar 24 10:49:09 VRB0C745BF0018 pluto: "IPsec_DUT2" #16: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.100:500
Mar 24 10:49:29 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Openswan (this version) VR-S1000_V2.09_D20140225-dirty ]
Mar 24 10:49:29 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:49:29 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:49:29 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:49:29 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:49:29 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:49:29 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:49:29 VRB0C745BF0018 pluto: "IPsec_DUT2" #17: responding to Main Mode
Mar 24 10:49:29 VRB0C745BF0018 pluto: "IPsec_DUT2" #17: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA2_256, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 10:49:29 VRB0C745BF0018 pluto: "IPsec_DUT2" #17: no acceptable Oakley Transform
Mar 24 10:49:29 VRB0C745BF0018 pluto: "IPsec_DUT2" #17: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.100:500
Mar 24 10:50:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:50:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:50:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:50:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:50:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:50:09 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:50:09 VRB0C745BF0018 pluto: "IPsec_DUT2" #18: responding to Main Mode
Mar 24 10:50:09 VRB0C745BF0018 pluto: "IPsec_DUT2" #18: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA2_256, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 10:50:09 VRB0C745BF0018 pluto: "IPsec_DUT2" #18: no acceptable Oakley Transform
Mar 24 10:50:09 VRB0C745BF0018 pluto: "IPsec_DUT2" #18: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.100:500
Mar 24 10:50:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Openswan (this version) VR-S1000_V2.09_D20140225-dirty ]
Mar 24 10:50:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:50:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:50:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:50:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:50:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:50:19 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:50:19 VRB0C745BF0018 pluto: "IPsec_DUT2" #19: responding to Main Mode
Mar 24 10:50:19 VRB0C745BF0018 pluto: "IPsec_DUT2" #19: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA2_256, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 10:50:19 VRB0C745BF0018 pluto: "IPsec_DUT2" #19: no acceptable Oakley Transform
Mar 24 10:50:19 VRB0C745BF0018 pluto: "IPsec_DUT2" #19: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.100:500
Mar 24 10:50:39 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Openswan (this version) VR-S1000_V2.09_D20140225-dirty ]
Mar 24 10:50:39 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:50:39 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:50:39 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:50:39 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:50:39 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:50:39 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:50:39 VRB0C745BF0018 pluto: "IPsec_DUT2" #20: responding to Main Mode
Mar 24 10:50:39 VRB0C745BF0018 pluto: "IPsec_DUT2" #20: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA2_256, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 10:50:39 VRB0C745BF0018 pluto: "IPsec_DUT2" #20: no acceptable Oakley Transform
Mar 24 10:50:39 VRB0C745BF0018 pluto: "IPsec_DUT2" #20: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.100:500
Web設定画面 設定箇所
VPN > IPsec > IPsecポリシー > IKEポリシー
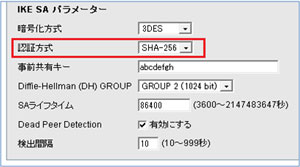
10.【失敗例】IKE policyの事前共有鍵の不一致でつながらない
DUT1側のログ
PC1→PC2宛のpingでIPsecのトリガとする。 (DUT1がイニシエーターとなる)
《IPsecパラメーター》
DUT1 IKEポリシー / PSK=abcdefgh1
DUT2 IKEポリシー / PSK=abcdefgh
他は IPsecウィザードのデフォルト値で設定
Mar 24 10:57:43 VRB0C745BF000E pluto: loading secrets from "/etc/ipsec.secrets"
Mar 24 10:57:44 VRB0C745BF000E janus_run: Starting janus watcher...
Mar 24 10:57:44 VRB0C745BF000E janus watcher[28345]: Starting Janus - Dynamic DNS watcher (Version 1.3)
Mar 24 10:57:55 VRB0C745BF000E pluto: initiate on demand from 192.168.100.100:8 to 192.168.101.100:0 proto=1 state: fos_start because: acquire
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: initiating Main Mode
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: received Vendor ID payload [Openswan (this version) VR-S1000_V2.09_D20140225-dirty ]
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: enabling possible NAT-traversal with method RFC 3947 (NAT-Traversal)
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: transition from state STATE_MAIN_I1 to state STATE_MAIN_I2
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: STATE_MAIN_I2: sent MI2, expecting MR2
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): no NAT detected
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: transition from state STATE_MAIN_I2 to state STATE_MAIN_I3
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: STATE_MAIN_I3: sent MI3, expecting MR3
Mar 24 10:57:55 VRB0C745BF000E pluto: "IPsec_test" #9: received 1 malformed payload notifies
Mar 24 10:58:05 VRB0C745BF000E pluto: "IPsec_test" #9: discarding duplicate packet; already STATE_MAIN_I3
Mar 24 10:58:25 VRB0C745BF000E pluto: "IPsec_test" #9: discarding duplicate packet; already STATE_MAIN_I3
Mar 24 10:58:25 VRB0C745BF000E pluto: "IPsec_test" #9: received 3 malformed payload notifies
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #9: starting keying attempt 2 of at most 3
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: initiating Main Mode to replace #9
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: received Vendor ID payload [Openswan (this version) VR-S1000_V2.09_D20140225-dirty ]
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: enabling possible NAT-traversal with method RFC 3947 (NAT-Traversal)
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: transition from state STATE_MAIN_I1 to state STATE_MAIN_I2
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: STATE_MAIN_I2: sent MI2, expecting MR2
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): no NAT detected
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: transition from state STATE_MAIN_I2 to state STATE_MAIN_I3
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: STATE_MAIN_I3: sent MI3, expecting MR3
Mar 24 10:59:05 VRB0C745BF000E pluto: "IPsec_test" #10: received 1 malformed payload notifies
Mar 24 10:59:15 VRB0C745BF000E pluto: "IPsec_test" #10: received 2 malformed payload notifies
Mar 24 10:59:15 VRB0C745BF000E pluto: "IPsec_test" #10: discarding duplicate packet; already STATE_MAIN_I3
Mar 24 10:59:35 VRB0C745BF000E pluto: "IPsec_test" #10: discarding duplicate packet; already STATE_MAIN_I3
Mar 24 10:59:35 VRB0C745BF000E pluto: "IPsec_test" #10: received 3 malformed payload notifies
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #10: starting keying attempt 3 of at most 3
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: initiating Main Mode to replace #10
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: received Vendor ID payload [Openswan (this version) VR-S1000_V2.09_D20140225-dirty ]
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: received Vendor ID payload [Dead Peer Detection]
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: enabling possible NAT-traversal with method RFC 3947 (NAT-Traversal)
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: transition from state STATE_MAIN_I1 to state STATE_MAIN_I2
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: STATE_MAIN_I2: sent MI2, expecting MR2
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): no NAT detected
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: transition from state STATE_MAIN_I2 to state STATE_MAIN_I3
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: STATE_MAIN_I3: sent MI3, expecting MR3
Mar 24 11:00:15 VRB0C745BF000E pluto: "IPsec_test" #11: received 1 malformed payload notifies
Mar 24 11:00:25 VRB0C745BF000E pluto: "IPsec_test" #11: received 2 malformed payload notifies
Mar 24 11:00:25 VRB0C745BF000E pluto: "IPsec_test" #11: discarding duplicate packet; already STATE_MAIN_I3
Mar 24 11:00:45 VRB0C745BF000E pluto: "IPsec_test" #11: received 3 malformed payload notifies
Mar 24 11:00:45 VRB0C745BF000E pluto: "IPsec_test" #11: discarding duplicate packet; already STATE_MAIN_I3
DUT2側のログ
MEMO
Mainモードで接続要求に応答しているが、Preshared secrets(事前共有鍵)の不一致により、認証に失敗しPhase1(ISAKMP SA)に失敗している
Mar 24 10:57:55 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:57:55 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:57:55 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:57:55 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:57:55 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:57:55 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:57:55 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: responding to Main Mode
Mar 24 10:57:55 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: transition from state STATE_MAIN_R0 to state STATE_MAIN_R1
Mar 24 10:57:55 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: STATE_MAIN_R1: sent MR1, expecting MI2
Mar 24 10:57:55 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): no NAT detected
Mar 24 10:57:55 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: transition from state STATE_MAIN_R1 to state STATE_MAIN_R2
Mar 24 10:57:55 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: STATE_MAIN_R2: sent MR2, expecting MI3
Mar 24 10:57:55 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: next payload type of ISAKMP Identification Payload has an unknown value: 68
Mar 24 10:57:55 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 10:57:55 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: sending notification PAYLOAD_MALFORMED to 172.27.0.100:500
Mar 24 10:58:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 10:58:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: sending notification PAYLOAD_MALFORMED to 172.27.0.100:500
Mar 24 10:58:25 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: next payload type of ISAKMP Identification Payload has an unknown value: 68
Mar 24 10:58:25 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 10:58:25 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: sending notification PAYLOAD_MALFORMED to 172.27.0.100:500
Mar 24 10:59:05 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 10:59:05 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 10:59:05 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 10:59:05 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 10:59:05 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 10:59:05 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: responding to Main Mode
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: transition from state STATE_MAIN_R0 to state STATE_MAIN_R1
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: STATE_MAIN_R1: sent MR1, expecting MI2
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #21: max number of retransmissions (2) reached STATE_MAIN_R2
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): no NAT detected
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: transition from state STATE_MAIN_R1 to state STATE_MAIN_R2
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: STATE_MAIN_R2: sent MR2, expecting MI3
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: next payload type of ISAKMP Identification Payload has an unknown value: 79
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 10:59:05 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: sending notification PAYLOAD_MALFORMED to 172.27.0.100:500
Mar 24 10:59:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: next payload type of ISAKMP Identification Payload has an unknown value: 79
Mar 24 10:59:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 10:59:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: sending notification PAYLOAD_MALFORMED to 172.27.0.100:500
Mar 24 10:59:35 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: next payload type of ISAKMP Identification Payload has an unknown value: 79
Mar 24 10:59:35 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 10:59:35 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: sending notification PAYLOAD_MALFORMED to 172.27.0.100:500
Mar 24 11:00:15 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [Dead Peer Detection]
Mar 24 11:00:15 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 11:00:15 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-03] meth=108, but already using method 115
Mar 24 11:00:15 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 11:00:15 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02] meth=107, but already using method 115
Mar 24 11:00:15 VRB0C745BF0018 pluto: packet from 172.27.0.100:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-00]
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: responding to Main Mode
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: transition from state STATE_MAIN_R0 to state STATE_MAIN_R1
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: STATE_MAIN_R1: sent MR1, expecting MI2
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #22: max number of retransmissions (2) reached STATE_MAIN_R2
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): no NAT detected
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: transition from state STATE_MAIN_R1 to state STATE_MAIN_R2
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: STATE_MAIN_R2: sent MR2, expecting MI3
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: next payload type of ISAKMP Identification Payload has an unknown value: 81
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 11:00:15 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: sending notification PAYLOAD_MALFORMED to 172.27.0.100:500
Mar 24 11:00:25 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: next payload type of ISAKMP Identification Payload has an unknown value: 81
Mar 24 11:00:25 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 11:00:25 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: sending notification PAYLOAD_MALFORMED to 172.27.0.100:500
Mar 24 11:00:45 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: next payload type of ISAKMP Identification Payload has an unknown value: 81
Mar 24 11:00:45 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 11:00:45 VRB0C745BF0018 pluto: "IPsec_DUT2" #23: sending notification PAYLOAD_MALFORMED to 172.27.0.100:500
Web設定画面 設定箇所
VPN > IPsec > IPsecポリシー > IKEポリシー
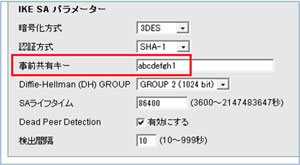
11. IKE policyのローカルアドレスが間違っていてつながらない
DUT1側のログ
本来 172.27.0.100 であるべきところを、172.27.0.10 と設定間違い。
PC1→PC2宛のpingでIPsecのトリガとする。
接続動作開始せず、特にログは出力されない。
DUT2側のログ
接続要求がないため、特にログは出力されない。
Web設定画面 設定箇所
VPN > IPsec > IPsecポリシー > IKEポリシー
このご質問の対象となる商品・OS・接続機器を表示
商品
OS・接続機器
チャット・LINEでのサポートについて
下記商品はチャット・LINEでのサポート対象外のため、電話またはメールにてお問合せいただきますようお願いいたします。
法人様向けネットワーク商品
ネットワーク対応ハードディスク(TeraStation)
<注意事項>
以下のいずれかに該当する場合、お客様の同意なくチャット・LINEでのサポートを終了させていただく場合がございます。ご了承ください。
同一のお客様から同一内容のお問合せ等の入力が複数あった場合
本サービスに関係のない画像・動画・スタンプ等が送信された場合
一定時間以上お客様からの返信がされない場合
営業時間
<オペレーター受付時間>
月~土・祝 9:30~21:00
日 9:30~17:30
※AIによる自動応答は24時間ご利用いただけます。
メールで相談について
個人向けWi-Fi/有線LAN製品、ストレージ製品のお客様にはメールで問い合わせいただく前にAIが問題解決のお手伝いを行います。
いずれかを選択して進んでください。
 Wi-Fi(無線LAN)
Wi-Fi(無線LAN) 有線LAN
有線LAN HDD(ハードディスク)・NAS
HDD(ハードディスク)・NAS SSD
SSD ブルーレイ/DVD/CDドライブ
ブルーレイ/DVD/CDドライブ メモリー
メモリー USBメモリー
USBメモリー メモリーカード・カードリーダー/ライター
メモリーカード・カードリーダー/ライター 映像/音響機器
映像/音響機器 ケーブル
ケーブル マウス・キーボード・入力機器
マウス・キーボード・入力機器 Webカメラ・ヘッドセット
Webカメラ・ヘッドセット スマートフォンアクセサリー
スマートフォンアクセサリー タブレットアクセサリー
タブレットアクセサリー 電源関連用品
電源関連用品 アクセサリー・収納
アクセサリー・収納 テレビアクセサリー
テレビアクセサリー その他周辺機器
その他周辺機器 法人向けWi-Fi(無線LAN)
法人向けWi-Fi(無線LAN) 法人向け有線LAN
法人向け有線LAN LTEルーター
LTEルーター 法人向けNAS・HDD
法人向けNAS・HDD SSD
SSD ブルーレイ/DVD/CDドライブ
ブルーレイ/DVD/CDドライブ 法人向けメモリー・組込み/OEM
法人向けメモリー・組込み/OEM 法人向けUSBメモリー
法人向けUSBメモリー メモリーカード・カードリーダー/ライター
メモリーカード・カードリーダー/ライター 映像/音響機器
映像/音響機器 法人向け液晶ディスプレイ
法人向け液晶ディスプレイ 法人向けケーブル
法人向けケーブル 法人向けマウス・キーボード・入力機器
法人向けマウス・キーボード・入力機器 法人向けヘッドセット
法人向けヘッドセット 法人向けスマートフォンアクセサリー
法人向けスマートフォンアクセサリー 法人向けタブレットアクセサリー
法人向けタブレットアクセサリー 法人向け電源関連用品
法人向け電源関連用品 法人向けアクセサリー・収納
法人向けアクセサリー・収納 テレビアクセサリー
テレビアクセサリー オフィスサプライ
オフィスサプライ その他周辺機器
その他周辺機器 データ消去
データ消去