VR-S1000のログの意味を教えてください/ログ出力例(L2TP/IPsec)
Q
VR-S1000のログの見方・読み方がわかりません。
ログからどのような情報を読み取ることができますか。
IPsecのログ出力例はこちら
A
想定するネットワーク構成
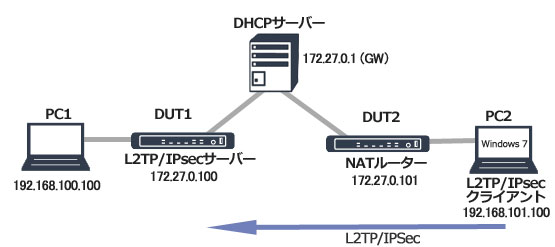
メインモード&識別子はWAN IPアドレスを使用
《L2TP/IPsecサーバー設定》
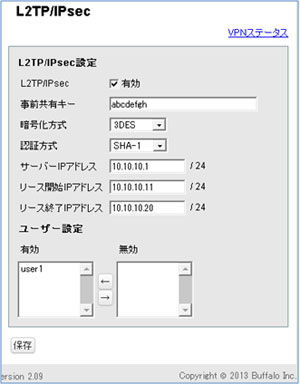
デバッグのポイント
まずは、Phase1/Phase2のどこまでできているかを確認
→「ISAKMP SA established」「IPsec SA established」が表示されているか確認
「IPsec SA established」が表示されていないなら、事前共有鍵/暗号化方式/認証方式の設定の見直しを実施
「IPsec SA established」が表示されているなら、VPNユーザーのアカウント(ユーザー名・パスワード)の設定を見直し
ログ出力例
VR-S1000のファームウェアVerによって出力されるログ情報が異なります。
下記はファームウェアVer.2.09以降でのログ出力例です。
1.【成功例】接続可能のログ 正常接続時
Mar 24 14:11:51 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:11:51 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:11:51 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:11:51 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:11:51 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:11:51 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): peer is NATed
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: transition from state STATE_MAIN_R1 to state STATE_MAIN_R2
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: STATE_MAIN_R2: sent MR2, expecting MI3
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: Main mode peer ID is ID_IPV4_ADDR: '192.168.101.100'
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #17: switched from "l2tp" to "l2tp"
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #17: deleting connection "l2tp" instance with peer 172.27.0.101 {isakmp=#0/ipsec=#0}
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #17: transition from state STATE_MAIN_R2 to state STATE_MAIN_R3
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #17: new NAT mapping for #17, was 172.27.0.101:500, now 172.27.0.101:4500
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #17: STATE_MAIN_R3: sent MR3, ISAKMP SA established {auth=OAKLEY_PRESHARED_KEY cipher=oakley_3des_cbc_192 prf=oakley_sha group=modp1024}
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #17: the peer proposed: 172.27.0.100/32:17/1701 -> 192.168.101.100/32:17/0
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #17: NAT-Traversal: received 2 NAT-OA. using first, ignoring others
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #18: responding to Quick Mode proposal {msgid:01000000}
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #18: us: 172.27.0.100:17/1701
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #18: them: 172.27.0.101[192.168.101.100]:17/1701===192.168.101.100/32
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #18: transition from state STATE_QUICK_R0 to state STATE_QUICK_R1
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #18: STATE_QUICK_R1: sent QR1, inbound IPsec SA installed, expecting QI2
Mar 24 14:11:51 VRB0C745BF000E pppd[22771]: Plugin /usr/lib/pptpd/pptpd-logwtmp.so loaded.
Mar 24 14:11:51 VRB0C745BF000E pppd[22771]: pptpd-logwtmp: $Version$
Mar 24 14:11:51 VRB0C745BF000E pppd[22771]: Plugin pppol2tp.so loaded.
Mar 24 14:11:51 VRB0C745BF000E pppd[22771]: pppd 2.4.5 started by root, uid 0
Mar 24 14:11:51 VRB0C745BF000E pppd[22771]: Using interface ppp0
Mar 24 14:11:51 VRB0C745BF000E pppd[22771]: Connect: ppp0 <-->
Mar 24 14:11:51 VRB0C745BF000E pppd[22771]: Overriding mtu 1500 to 1400
Mar 24 14:11:51 VRB0C745BF000E pppd[22771]: Overriding mru 1500 to mtu value 1400
Mar 24 14:11:51 VRB0C745BF000E pppd[22771]: Warning - secret file /etc/ppp/pap-secrets has world and/or group access
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #18: transition from state STATE_QUICK_R1 to state STATE_QUICK_R2
Mar 24 14:11:51 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #18: STATE_QUICK_R2: IPsec SA established
transport
mode {ESP=>0x935399b2 <0x8289e262 xfrm=AES_128-HMAC_SHA1 NATOA=192.168.101.100 NATD=172.27.0.101:4500 DPD=none}
Mar 24 14:11:54 VRB0C745BF000E pppd[22771]: Warning - secret file /etc/ppp/chap-secrets has world and/or group access
Mar 24 14:11:54 VRB0C745BF000E pppd[22771]: Unsupported protocol 'IPv6 Control Protocol' (0x8057) received
Mar 24 14:11:54 VRB0C745BF000E pppd[22771]: Unsupported protocol 'Compression Control Protocol' (0x80fd) received
Mar 24 14:11:54 VRB0C745BF000E pppd[22771]: Cannot determine ethernet address for proxy ARP
Mar 24 14:11:54 VRB0C745BF000E pppd[22771]: local IP address 10.10.10.1
Mar 24 14:11:54 VRB0C745BF000E pppd[22771]: remote IP address 10.10.10.11
Mar 24 14:11:54 VRB0C745BF000E pppd[22771]: pptpd-logwtmp.so ip-up ppp0 user1
Mar 24 14:11:55 VRB0C745BF000E PPPoE: PPPoE updates IP address.
2.【成功例】接続可能のログ 正常切断時 - Windows側で、「切断する」処理を明示的に実行した場合
Mar 24 14:14:18 VRB0C745BF000E pppd[22771]: LCP terminated by peer ('W;;^@<M-Mt^@^@^@^@)
Mar 24 14:14:18 VRB0C745BF000E pppd[22771]: pptpd-logwtmp.so ip-down ppp0
Mar 24 14:14:18 VRB0C745BF000E pppd[22771]: Connect time 2.4 minutes.
Mar 24 14:14:18 VRB0C745BF000E pppd[22771]: Sent 1814 bytes, received 13749 bytes.
Mar 24 14:14:18 VRB0C745BF000E pppd[22771]: Overriding mtu 1500 to 1400
Mar 24 14:14:18 VRB0C745BF000E pppd[22771]: Overriding mru 1500 to mtu value 1400
Mar 24 14:14:18 VRB0C745BF000E xl2tpd[21092]: control_finish: Connection closed to 172.27.0.101, serial 0 ()
Mar 24 14:14:18 VRB0C745BF000E pppd[22771]: Terminating on signal 15
Mar 24 14:14:18 VRB0C745BF000E xl2tpd[21092]: control_finish: Connection closed to 172.27.0.101, port 1701 (), Local: 9561, Remote: 11
Mar 24 14:14:18 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #17: ERROR: netlink XFRM_MSG_DELPOLICY response for flow eroute_connection delete included errno 2: No such file or directory
Mar 24 14:14:18 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #17: received and ignored informational message
Mar 24 14:14:18 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #17: received Delete SA payload: deleting ISAKMP State #17
Mar 24 14:14:18 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101: deleting connection "l2tp" instance with peer 172.27.0.101 {isakmp=#0/ipsec=#0}
Mar 24 14:14:18 VRB0C745BF000E pluto: packet from 172.27.0.101:4500: received and ignored informational message
Mar 24 14:14:21 VRB0C745BF000E pppd[22771]: Connection terminated.
Mar 24 14:14:21 VRB0C745BF000E pppd[22771]: Modem hangup
Mar 24 14:14:21 VRB0C745BF000E pppd[22771]: Exit.
3.【失敗例】アカウント間違い
Mar 24 14:16:16 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:16:16 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:16:16 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:16:16 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:16:16 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:16:16 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: transition from state STATE_MAIN_R0 to state STATE_MAIN_R1
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: STATE_MAIN_R1: sent MR1, expecting MI2
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): peer is NATed
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: transition from state STATE_MAIN_R1 to state STATE_MAIN_R2
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: STATE_MAIN_R2: sent MR2, expecting MI3
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: Main mode peer ID is ID_IPV4_ADDR: '192.168.101.100'
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #19: switched from "l2tp" to "l2tp"
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: deleting connection "l2tp" instance with peer 172.27.0.101 {isakmp=#0/ipsec=#0}
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: transition from state STATE_MAIN_R2 to state STATE_MAIN_R3
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: new NAT mapping for #19, was 172.27.0.101:500, now 172.27.0.101:4500
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: STATE_MAIN_R3: sent MR3, ISAKMP SA established {auth=OAKLEY_PRESHARED_KEY cipher=oakley_3des_cbc_192 prf=oakley_sha group=modp1024}
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: the peer proposed: 172.27.0.100/32:17/1701 -> 192.168.101.100/32:17/0
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: NAT-Traversal: received 2 NAT-OA. using first, ignoring others
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #20: responding to Quick Mode proposal {msgid:01000000}
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #20: us: 172.27.0.100:17/1701
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #20: them: 172.27.0.101[192.168.101.100]:17/1701===192.168.101.100/32
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #20: transition from state STATE_QUICK_R0 to state STATE_QUICK_R1
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #20: STATE_QUICK_R1: sent QR1, inbound IPsec SA installed, expecting QI2
Mar 24 14:16:16 VRB0C745BF000E xl2tpd[21092]: Call established with 172.27.0.101, Local: 33116, Remote: 1, Serial: 0
Mar 24 14:16:16 VRB0C745BF000E pppd[29560]: Plugin /usr/lib/pptpd/pptpd-logwtmp.so loaded.
Mar 24 14:16:16 VRB0C745BF000E pppd[29560]: pptpd-logwtmp: $Version$
Mar 24 14:16:16 VRB0C745BF000E pppd[29560]: Plugin pppol2tp.so loaded.
Mar 24 14:16:16 VRB0C745BF000E pppd[29560]: pppd 2.4.5 started by root, uid 0
Mar 24 14:16:16 VRB0C745BF000E pppd[29560]: Using interface ppp0
Mar 24 14:16:16 VRB0C745BF000E pppd[29560]: Connect: ppp0 <-->
Mar 24 14:16:16 VRB0C745BF000E pppd[29560]: Overriding mtu 1500 to 1400
Mar 24 14:16:16 VRB0C745BF000E pppd[29560]: Overriding mru 1500 to mtu value 1400
Mar 24 14:16:16 VRB0C745BF000E pppd[29560]: Warning - secret file /etc/ppp/pap-secrets has world and/or group access
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #20: transition from state STATE_QUICK_R1 to state STATE_QUICK_R2
Mar 24 14:16:16 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #20: STATE_QUICK_R2: IPsec SA established transport mode {ESP=>0x0e168471 <0x6d0a4db6 xfrm=AES_128-HMAC_SHA1 NATOA=192.168.101.100 NATD=172.27.0.101:4500 DPD=none}
Mar 24 14:16:19 VRB0C745BF000E pppd[29560]: Warning - secret file /etc/ppp/chap-secrets has world and/or group access
Mar 24 14:16:19 VRB0C745BF000E pppd[29560]: No CHAP secret found for authenticating user2
Mar 24 14:16:19 VRB0C745BF000E pppd[29560]: Peer user2 failed CHAP authentication
Mar 24 14:16:19 VRB0C745BF000E pppd[29560]: Overriding mtu 1500 to 1400
Mar 24 14:16:19 VRB0C745BF000E pppd[29560]: Overriding mru 1500 to mtu value 1400
Mar 24 14:16:19 VRB0C745BF000E pppd[29560]: Connection terminated.
Mar 24 14:16:19 VRB0C745BF000E xl2tpd[21092]: control_finish: Connection closed to 172.27.0.101, serial 0 ()
Mar 24 14:16:19 VRB0C745BF000E xl2tpd[21092]: control_finish: Connection closed to 172.27.0.101, port 1701 (), Local: 55195, Remote: 12
Mar 24 14:16:19 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: received Delete SA(0x0e168471) payload: deleting IPSEC State #20
Mar 24 14:16:19 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: ERROR: netlink XFRM_MSG_DELPOLICY response for flow eroute_connection delete included errno 2: No such file or directory
Mar 24 14:16:19 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: received and ignored informational message
Mar 24 14:16:19 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #19: received Delete SA payload: deleting ISAKMP State #19
Mar 24 14:16:19 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101: deleting connection "l2tp" instance with peer 172.27.0.101 {isakmp=#0/ipsec=#0}
Mar 24 14:16:19 VRB0C745BF000E pluto: packet from 172.27.0.101:4500: received and ignored informational message
Mar 24 14:16:19 VRB0C745BF000E pppd[29560]: Exit.
4.【失敗例】パスワード間違い
Windowsクライアント側で、user1に対するパスワードを誤って設定した場合
→Windows上では、「エラー619」となり接続できない。
Mar 24 14:18:53 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:18:53 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:18:53 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:18:53 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:18:53 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:18:53 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: transition from state STATE_MAIN_R0 to state STATE_MAIN_R1
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: STATE_MAIN_R1: sent MR1, expecting MI2
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): peer is NATed
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: transition from state STATE_MAIN_R1 to state STATE_MAIN_R2
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: STATE_MAIN_R2: sent MR2, expecting MI3
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: Main mode peer ID is ID_IPV4_ADDR: '192.168.101.100'
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[13] 172.27.0.101 #29: switched from "l2tp" to "l2tp"
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: deleting connection "l2tp" instance with peer 172.27.0.101 {isakmp=#0/ipsec=#0}
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: transition from state STATE_MAIN_R2 to state STATE_MAIN_R3
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: new NAT mapping for #29, was 172.27.0.101:500, now 172.27.0.101:4500
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: STATE_MAIN_R3: sent MR3, ISAKMP SA established {auth=OAKLEY_PRESHARED_KEY cipher=oakley_3des_cbc_192 prf=oakley_sha group=modp1024}
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: the peer proposed: 172.27.0.100/32:17/1701 -> 192.168.101.100/32:17/0
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: NAT-Traversal: received 2 NAT-OA. using first, ignoring others
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #30: responding to Quick Mode proposal {msgid:01000000}
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #30: us: 172.27.0.100:17/1701
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #30: them: 172.27.0.101[192.168.101.100]:17/1701===192.168.101.100/32
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #30: transition from state STATE_QUICK_R0 to state STATE_QUICK_R1
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #30: STATE_QUICK_R1: sent QR1, inbound IPsec SA installed, expecting QI2
Mar 24 14:18:53 VRB0C745BF000E pppd[1427]: Plugin /usr/lib/pptpd/pptpd-logwtmp.so loaded.
Mar 24 14:18:53 VRB0C745BF000E pppd[1427]: pptpd-logwtmp: $Version$
Mar 24 14:18:53 VRB0C745BF000E pppd[1427]: Plugin pppol2tp.so loaded.
Mar 24 14:18:53 VRB0C745BF000E pppd[1427]: pppd 2.4.5 started by root, uid 0
Mar 24 14:18:53 VRB0C745BF000E pppd[1427]: Using interface ppp0
Mar 24 14:18:53 VRB0C745BF000E pppd[1427]: Connect: ppp0 <-->
Mar 24 14:18:53 VRB0C745BF000E pppd[1427]: Overriding mtu 1500 to 1400
Mar 24 14:18:53 VRB0C745BF000E pppd[1427]: Overriding mru 1500 to mtu value 1400
Mar 24 14:18:53 VRB0C745BF000E pppd[1427]: Warning - secret file /etc/ppp/pap-secrets has world and/or group access
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #30: transition from state STATE_QUICK_R1 to state STATE_QUICK_R2
Mar 24 14:18:53 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #30: STATE_QUICK_R2: IPsec SA established transport mode {ESP=>0x86d02cad <0x390e7248 xfrm=AES_128-HMAC_SHA1 NATOA=192.168.101.100 NATD=172.27.0.101:4500 DPD=none}
Mar 24 14:18:56 VRB0C745BF000E pppd[1427]: Warning - secret file /etc/ppp/chap-secrets has world and/or group access
Mar 24 14:18:56 VRB0C745BF000E pppd[1427]: Peer user1 failed CHAP authentication
Mar 24 14:18:56 VRB0C745BF000E pppd[1427]: Overriding mtu 1500 to 1400
Mar 24 14:18:56 VRB0C745BF000E pppd[1427]: Overriding mru 1500 to mtu value 1400
Mar 24 14:18:56 VRB0C745BF000E pppd[1427]: Connection terminated.
Mar 24 14:18:56 VRB0C745BF000E pppd[1427]: Exit.
Mar 24 14:18:56 VRB0C745BF000E xl2tpd[21092]: call_close: Call 47036 to 172.27.0.101 disconnected
Mar 24 14:18:56 VRB0C745BF000E xl2tpd[21092]: control_finish: Connection closed to 172.27.0.101, port 1701 (), Local: 41393, Remote: 17
Mar 24 14:18:56 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: received Delete SA(0x86d02cad) payload: deleting IPSEC State #30
Mar 24 14:18:56 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: ERROR: netlink XFRM_MSG_DELPOLICY response for flow eroute_connection delete included errno 2: No such file or directory
Mar 24 14:18:56 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: received and ignored informational message
Mar 24 14:18:56 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101 #29: received Delete SA payload: deleting ISAKMP State #29
Mar 24 14:18:56 VRB0C745BF000E pluto: "l2tp"[14] 172.27.0.101: deleting connection "l2tp" instance with peer 172.27.0.101 {isakmp=#0/ipsec=#0}
Mar 24 14:18:56 VRB0C745BF000E pluto: packet from 172.27.0.101:4500: received and ignored informational message
5.【失敗例】事前共有キー間違い
Windowsクライアント側で、事前共有鍵を誤って設定した場合
→Windows上では、「エラー789」となり接続できない。
Mar 24 13:54:22 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 13:54:22 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 13:54:22 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 13:54:22 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 13:54:22 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 13:54:22 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: NAT-Traversal: Result using draft-ietf-ipsec-nat-t-ike (MacOS X): peer is NATed
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: transition from state STATE_MAIN_R1 to state STATE_MAIN_R2
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: STATE_MAIN_R2: sent MR2, expecting MI3
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: next payload type of ISAKMP Identification Payload has an unknown value: 221
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 13:54:22 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: sending notification PAYLOAD_MALFORMED to 172.27.0.101:500
Mar 24 13:54:24 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: next payload type of ISAKMP Identification Payload has an unknown value: 221
Mar 24 13:54:24 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 13:54:24 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: sending notification PAYLOAD_MALFORMED to 172.27.0.101:500
Mar 24 13:54:27 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: next payload type of ISAKMP Identification Payload has an unknown value: 221
Mar 24 13:54:27 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: probable authentication failure (mismatch of preshared secrets?):
malformed payload in packet
Mar 24 13:54:27 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: sending notification PAYLOAD_MALFORMED to 172.27.0.101:500
Mar 24 13:54:31 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: next payload type of ISAKMP Identification Payload has an unknown value: 221
Mar 24 13:54:31 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 13:54:31 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: sending notification PAYLOAD_MALFORMED to 172.27.0.101:500
Mar 24 13:54:40 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: next payload type of ISAKMP Identification Payload has an unknown value: 221
Mar 24 13:54:40 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 13:54:40 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: sending notification PAYLOAD_MALFORMED to 172.27.0.101:500
Mar 24 13:54:57 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: next payload type of ISAKMP Identification Payload has an unknown value: 221
Mar 24 13:54:57 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 13:54:57 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: sending notification PAYLOAD_MALFORMED to 172.27.0.101:500
Mar 24 13:55:13 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: next payload type of ISAKMP Identification Payload has an unknown value: 221
Mar 24 13:55:13 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: probable authentication failure (mismatch of preshared secrets?): malformed payload in packet
Mar 24 13:55:13 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: sending notification PAYLOAD_MALFORMED to 172.27.0.101:500
Mar 24 13:55:32 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101 #17: max number of retransmissions (2) reached STATE_MAIN_R2
Mar 24 13:55:32 VRB0C745BF000E pluto: "l2tp"[16] 172.27.0.101: deleting connection "l2tp" instance with peer 172.27.0.101 {isakmp=#0/ipsec=#0}
6.【失敗例】暗号化方式間違い
VR-S1000側で、暗号化方式を3DES以外(例:AES-128)に設定した場合
→Windows上では、「エラー789」となり接続できない。
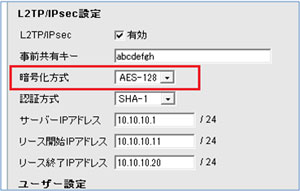
Mar 24 14:06:18 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:06:18 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:06:18 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:06:18 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:06:18 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:06:18 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:06:18 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #7: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:06:18 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #7: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:06:18 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #7: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:06:18 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #7: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:06:18 VRB0C745BF000E pluto: "l2tp"[1] 172.27.0.101 #7: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:06:20 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS NT5 ISAKMPOAKLEY 00000008]
Mar 24 14:06:20 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:06:20 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:06:20 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:06:20 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:06:20 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:06:20 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:06:20 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #8: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:06:20 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #8: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:06:20 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #8: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:06:20 VRB0C745BF000E pluto: "l2tp"[2] 172.27.0.101 #8: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:06:23 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS NT5 ISAKMPOAKLEY 00000008]
Mar 24 14:06:23 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:06:23 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:06:23 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:06:23 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:06:23 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:06:23 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:06:23 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #9: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:06:23 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #9: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:06:23 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #9: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:06:23 VRB0C745BF000E pluto: "l2tp"[3] 172.27.0.101 #9: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:06:27 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS NT5 ISAKMPOAKLEY 00000008]
Mar 24 14:06:27 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:06:27 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:06:27 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:06:27 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:06:27 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:06:27 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:06:27 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #10: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:06:27 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #10: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:06:27 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #10: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:06:27 VRB0C745BF000E pluto: "l2tp"[4] 172.27.0.101 #10: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:08:24 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS NT5 ISAKMPOAKLEY 00000008]
Mar 24 14:08:24 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:08:24 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:08:24 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:08:24 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:08:24 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:08:24 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:08:24 VRB0C745BF000E pluto: "l2tp"[5] 172.27.0.101 #11: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:08:24 VRB0C745BF000E pluto: "l2tp"[5] 172.27.0.101 #11: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:08:24 VRB0C745BF000E pluto: "l2tp"[5] 172.27.0.101 #11: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:08:24 VRB0C745BF000E pluto: "l2tp"[5] 172.27.0.101 #11: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:08:26 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS NT5 ISAKMPOAKLEY 00000008]
Mar 24 14:08:26 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:08:26 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:08:26 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:08:26 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:08:26 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:08:26 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:08:26 VRB0C745BF000E pluto: "l2tp"[6] 172.27.0.101 #12: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:08:26 VRB0C745BF000E pluto: "l2tp"[6] 172.27.0.101 #12: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:08:26 VRB0C745BF000E pluto: "l2tp"[6] 172.27.0.101 #12: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:08:26 VRB0C745BF000E pluto: "l2tp"[6] 172.27.0.101 #12: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:08:29 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS NT5 ISAKMPOAKLEY 00000008]
Mar 24 14:08:29 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:08:29 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:08:29 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:08:29 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:08:29 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:08:29 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:08:29 VRB0C745BF000E pluto: "l2tp"[7] 172.27.0.101 #13: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:08:29 VRB0C745BF000E pluto: "l2tp"[7] 172.27.0.101 #13: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:08:29 VRB0C745BF000E pluto: "l2tp"[7] 172.27.0.101 #13: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:08:29 VRB0C745BF000E pluto: "l2tp"[7] 172.27.0.101 #13: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:08:34 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS NT5 ISAKMPOAKLEY 00000008]
Mar 24 14:08:34 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [RFC 3947] method set to=115
Mar 24 14:08:34 VRB0C745BF000E pluto: packet from 172.27.0.101:500: received Vendor ID payload [draft-ietf-ipsec-nat-t-ike-02_n] meth=106, but already using method 115
Mar 24 14:08:34 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [FRAGMENTATION]
Mar 24 14:08:34 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [MS-Negotiation Discovery Capable]
Mar 24 14:08:34 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [Vid-Initial-Contact]
Mar 24 14:08:34 VRB0C745BF000E pluto: packet from 172.27.0.101:500: ignoring Vendor ID payload [IKE CGA version 1]
Mar 24 14:08:34 VRB0C745BF000E pluto: "l2tp"[8] 172.27.0.101 #14: responding to Main Mode from unknown peer 172.27.0.101
Mar 24 14:08:34 VRB0C745BF000E pluto: "l2tp"[8] 172.27.0.101 #14: OAKLEY_GROUP 20 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:08:34 VRB0C745BF000E pluto: "l2tp"[8] 172.27.0.101 #14: OAKLEY_GROUP 19 not supported. Attribute OAKLEY_GROUP_DESCRIPTION
Mar 24 14:08:34 VRB0C745BF000E pluto: "l2tp"[8] 172.27.0.101 #14: Oakley Transform [OAKLEY_AES_CBC (256), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:08:34 VRB0C745BF000E pluto: "l2tp"[8] 172.27.0.101 #14: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA1, OAKLEY_GROUP_MODP2048] refused due to strict flag
Mar 24 14:08:34 VRB0C745BF000E pluto: "l2tp"[8] 172.27.0.101 #14: Oakley Transform [OAKLEY_3DES_CBC (192), OAKLEY_SHA1, OAKLEY_GROUP_MODP1024] refused due to strict flag
Mar 24 14:08:34 VRB0C745BF000E pluto: "l2tp"[8] 172.27.0.101 #14: no acceptable Oakley Transform
Mar 24 14:08:34 VRB0C745BF000E pluto: "l2tp"[8] 172.27.0.101 #14: sending notification NO_PROPOSAL_CHOSEN to 172.27.0.101:500
Mar 24 14:08:34 VRB0C745BF000E pluto: "l2tp"[8] 172.27.0.101: deleting connection "l2tp" instance with peer 172.27.0.101 {isakmp=#0/ipsec=#0}
このご質問の対象となる商品・OS・接続機器を表示
商品
OS・接続機器
チャット・LINEでのサポートについて
下記商品はチャット・LINEでのサポート対象外のため、電話またはメールにてお問合せいただきますようお願いいたします。
法人様向けネットワーク商品
ネットワーク対応ハードディスク(TeraStation)
<注意事項>
以下のいずれかに該当する場合、お客様の同意なくチャット・LINEでのサポートを終了させていただく場合がございます。ご了承ください。
同一のお客様から同一内容のお問合せ等の入力が複数あった場合
本サービスに関係のない画像・動画・スタンプ等が送信された場合
一定時間以上お客様からの返信がされない場合
営業時間
<オペレーター受付時間>
月~土・祝 9:30~21:00
日 9:30~17:30
※AIによる自動応答は24時間ご利用いただけます。
メールで相談について
個人向けWi-Fi/有線LAN製品、ストレージ製品のお客様にはメールで問い合わせいただく前にAIが問題解決のお手伝いを行います。
いずれかを選択して進んでください。
 Wi-Fi(無線LAN)
Wi-Fi(無線LAN) 有線LAN
有線LAN HDD(ハードディスク)・NAS
HDD(ハードディスク)・NAS SSD
SSD ブルーレイ/DVD/CDドライブ
ブルーレイ/DVD/CDドライブ メモリー
メモリー USBメモリー
USBメモリー メモリーカード・カードリーダー/ライター
メモリーカード・カードリーダー/ライター 映像/音響機器
映像/音響機器 ケーブル
ケーブル マウス・キーボード・入力機器
マウス・キーボード・入力機器 Webカメラ・ヘッドセット
Webカメラ・ヘッドセット スマートフォンアクセサリー
スマートフォンアクセサリー タブレットアクセサリー
タブレットアクセサリー 電源関連用品
電源関連用品 アクセサリー・収納
アクセサリー・収納 テレビアクセサリー
テレビアクセサリー その他周辺機器
その他周辺機器 法人向けWi-Fi(無線LAN)
法人向けWi-Fi(無線LAN) 法人向け有線LAN
法人向け有線LAN 法人向けルーター
法人向けルーター 法人向けNAS・HDD
法人向けNAS・HDD SSD
SSD ブルーレイ/DVD/CDドライブ
ブルーレイ/DVD/CDドライブ 法人向けメモリー・組込み/OEM
法人向けメモリー・組込み/OEM 法人向けUSBメモリー
法人向けUSBメモリー メモリーカード・カードリーダー/ライター
メモリーカード・カードリーダー/ライター 映像/音響機器
映像/音響機器 法人向け液晶ディスプレイ
法人向け液晶ディスプレイ 法人向けケーブル
法人向けケーブル 法人向けマウス・キーボード・入力機器
法人向けマウス・キーボード・入力機器 法人向けヘッドセット
法人向けヘッドセット 法人向けスマートフォンアクセサリー
法人向けスマートフォンアクセサリー 法人向けタブレットアクセサリー
法人向けタブレットアクセサリー 法人向け電源関連用品
法人向け電源関連用品 法人向けアクセサリー・収納
法人向けアクセサリー・収納 テレビアクセサリー
テレビアクセサリー オフィスサプライ
オフィスサプライ その他周辺機器
その他周辺機器 データ消去
データ消去